Most Salesforce orgs accumulate technical debt invisibly until a migration fails or a critical business process breaks. By then, you’re looking at 6-12 month recovery timelines and seven-figure remediation costs. The problem isn’t that technical debt exists. Every enterprise platform has it. The problem is that most organizations don’t have a salesforce technical debt assessment framework to quantify the risk before it becomes a crisis.
Why Standard Audits Miss the Real Risk
The typical Salesforce health check runs a security review, counts unused fields, and generates a report showing green checkmarks. That approach misses the architectural debt that actually breaks platforms at scale.
Technical debt isn’t about code quality in isolation. It’s about the compounding cost of past decisions that constrain future capability. A Process Builder with 50 criteria? That’s a migration blocker that will force you to rewrite business logic during your next major release. A custom integration built on SOAP APIs? That’s a single point of failure that can’t scale past 10,000 daily transactions.
In practice, the debt that matters falls into four categories: architectural constraints (patterns that limit scale or integration), deprecated technology (features Salesforce will stop supporting), process fragility (automations that break under edge cases), and data integrity gaps (inconsistencies that corrupt downstream systems). Standard audits check for the second category. Enterprise risk lives in the other three.
The Four-Layer Assessment Model
A systematic technical debt assessment examines the platform through four lenses, each revealing different failure modes.
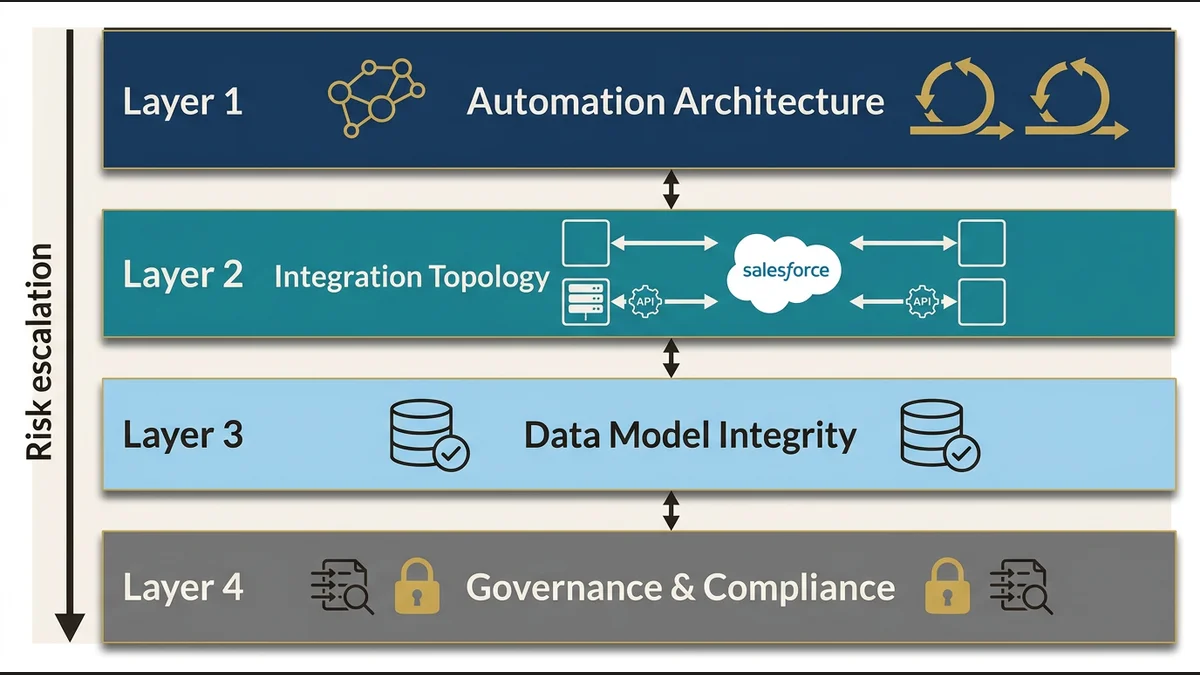
Layer 1: Automation Architecture. Map every automation (Flow, Apex triggers, Process Builder, Workflow Rules) and trace their execution paths. The goal isn’t counting automations. The goal is identifying recursive patterns, order-of-execution conflicts, and governor limit exposure. An org with 200 Flows isn’t inherently risky. An org with 15 Flows that all fire on the same object update and call each other recursively is a time bomb. Document which automations modify records that trigger other automations. Identify any process that approaches governor limits under normal load. Flag any automation that lacks error handling or retry logic.
Layer 2: Integration Topology. Document every system that reads from or writes to Salesforce. Not just the named integrations; every API consumer, every middleware layer, every scheduled job. The risk pattern here is tight coupling. If an external system expects Salesforce data in a specific format and that format is hardcoded in 40 Apex classes, you can’t refactor the data model without breaking the integration. Map the dependency chain: which external systems would fail if you changed a field API name, modified a picklist, or restructured an object relationship? Quantify the blast radius of common changes.
Layer 3: Data Model Complexity. Technical debt in the data model manifests as schema that no longer matches business reality. Count objects with 300+ custom fields where only 40% are actively used. Identify lookup relationships that create circular dependencies. Document any object with 15+ record types. That’s usually a sign that the object is modeling multiple business entities that should be separate. The specific risk is migration cost. Complex schemas with high field counts and deep relationship hierarchies take 3-5x longer to migrate than normalized models. If you’re planning a merger, acquisition, or platform consolidation, data model debt directly translates to timeline risk.
Layer 4: Governance Gaps. This layer examines the organizational patterns that allow debt to accumulate. How many developers have deployment access? Is there a code review process? Are there naming conventions for custom fields and objects? Do you have a change management process that requires impact analysis before schema changes? Governance gaps don’t cause immediate failures. They cause debt to compound exponentially because every team makes local optimizations that create global constraints. An org with 15 development teams and no architectural review board will accumulate debt 10x faster than an org with centralized governance.
Quantifying the Risk Score
The assessment framework produces a risk score across three dimensions: migration complexity, operational fragility, and technical obsolescence. Each dimension uses specific metrics.
Migration complexity measures how difficult it would be to move this org to a new instance or merge it with another org. High field counts, custom metadata dependencies, and hardcoded IDs all increase migration complexity. A typical scoring model: 1 point per 100 custom fields, 2 points per object with circular lookups, 5 points per integration with hardcoded record IDs, 10 points per Process Builder with 30+ criteria. An org scoring above 200 points will require 12+ months for a clean migration.
Operational fragility measures how likely the org is to experience production failures under normal business conditions. Count automations without error handling, integrations without retry logic, and processes that approach governor limits at 80% of current transaction volume. The critical threshold is any automation that fails more than once per month in production. If you’re seeing recurring failures in the same automation, that’s not a bug. That’s architectural fragility.
Technical obsolescence measures exposure to deprecated features and unsupported patterns. Salesforce announces deprecation timelines years in advance, but most orgs don’t track them systematically. As of 2026, the high-risk items are: any remaining Workflow Rules or Process Builder (Flow is the supported automation framework), SOAP API integrations (REST is the current standard), and Classic Email Templates (Lightning Email Templates are the replacement). Score 1 point per deprecated feature instance. Above 50 points, you’re facing a forced migration within 18 months.
The Remediation Roadmap
The assessment produces a prioritized backlog, not a “fix everything” mandate. Remediation follows a specific sequence.
Phase 1: Eliminate production risk. Fix any automation that’s failing in production, any integration approaching governor limits, and any process without error handling. This phase typically takes 4-8 weeks and prevents immediate business disruption. The goal is stability, not perfection.
Phase 2: Address deprecation exposure. Migrate off any feature Salesforce has announced end-of-life dates for. This work is time-bounded. If Workflow Rules are being retired in 12 months, you have 12 months. Start with the most complex migrations first because they’ll take longer than you estimate. A 200-criteria Process Builder doesn’t convert to Flow in a week.
Phase 3: Reduce architectural constraints. Refactor patterns that limit future capability. Decouple tightly-coupled integrations. Normalize complex data models. Implement governance processes to prevent new debt. This phase is ongoing. It’s not a project, it’s a practice. Allocate 20% of platform capacity to debt reduction every quarter.
The common mistake is trying to do all three phases simultaneously. That approach fails because it creates too much change risk. Production stability comes first. Deprecation timelines come second. Architectural improvement comes third.
When to Bring in External Architecture
Most organizations can execute Phase 1 internally. Phase 2 requires Salesforce-specific expertise: you need someone who knows the migration path from Process Builder to Flow and can architect the equivalent logic without introducing new technical debt. Phase 3 requires enterprise architecture experience, someone who’s seen the failure patterns at scale and can design governance that actually works.
The decision point is complexity and timeline. If your assessment shows 200+ points of migration complexity and you’re planning a merger in 12 months, you don’t have time to learn through trial and error. If your org is experiencing weekly production failures from automation conflicts, you need someone who can map the execution order and identify the root cause in days, not months.
In practice, the highest-ROI engagement model is a 2-week assessment followed by a 90-day remediation sprint focused on Phase 1 and Phase 2. That gets you to stable and supported. Phase 3 can happen incrementally with internal teams once the immediate risk is contained.
Key Takeaways
- Technical debt assessment requires examining four layers: automation architecture, integration topology, data model complexity, and governance gaps. Standard health checks only surface a fraction of the risk
- Quantify debt across three dimensions: migration complexity (cost to move), operational fragility (likelihood of failure), and technical obsolescence (forced timeline pressure)
- Remediation follows a strict sequence: stabilize production first, address deprecation timelines second, improve architecture third. Attempting all three simultaneously creates unmanageable change risk
- The assessment produces a risk score that directly predicts migration timelines and recovery costs. Orgs above 200 points require 12+ months for clean migrations
- Most organizations can handle stability fixes internally but need specialized expertise for deprecation migrations and architectural refactoring at enterprise scale
Need help with org health & recovery architecture?
Diagnose failing Salesforce implementations, eliminate technical debt, and architect recovery plans that get derailed projects back on track within 90 days.
Related Articles

Dette Technique Salesforce : Audit et Remédiation
Comment auditer et remédier la dette technique Salesforce avant qu'elle bloque vos projets IA. Méthode, outils et priorités pour les DSI.
Salesforce Architecture Review Checklist
A senior architect's framework for auditing Salesforce orgs: what to check, what breaks at scale, and where hidden risk lives.
